Security in a MFA world
There’s no question that the state of password security is problematic and has been for a long time. When humans pick their own passwords, too often they are easy to guess or predict. When we are assigned or forced to create passwords that are hard to remember, too often they are written down where others can see them.
When we are forced to change passwords, too often we’ll make a small and predictable alteration to the existing passwords, and/or forget the new passwords. These can all lead to decreasing the security of your password and when passwords or their corresponding hashes are stolen, it can be difficult to detect or restrict their unauthorized use.
Why We Should Use MFA?
It is evident that we need a better way to create and manage passwords. Banks and big corporates hit on the solution years ago, a second form of authentication aka Multi Factor Authentication (MFA). MFA relies on two or more things:
- Something we know (a password),
- Something we have (Time-based One-Time Password (TOTP), Short Message Service (SMS), Electronic Mail (Email), Push Notifications, Phone Calls) or
- Something we are (biometric information).
In this situation, implementing MFA will prevent hackers from gaining access to your accounts even if your password is known or cracked. The extra layer of protection that MFA offers ensures that your account is more secure.
The New Problem
Most people will have at least some form of MFA security on accounts such as Banking & Financial, E-commerce, Email and Social Media. We can manage this as individuals by using Third party applications like 2STP and Google Authenticator, but what about businesses and the systems they deal with? Increasingly businesses are required to have accounts on multiple third party systems in which employees share passwords to these accounts.
The systems that do provide MFA, do it differently. They now require an additional layer of administration on top of usernames and passwords. These extra layers make them more secure, but are we compromising productivity due to being shackled by security? This can sometimes be the case but we can now manage it.
The New Way
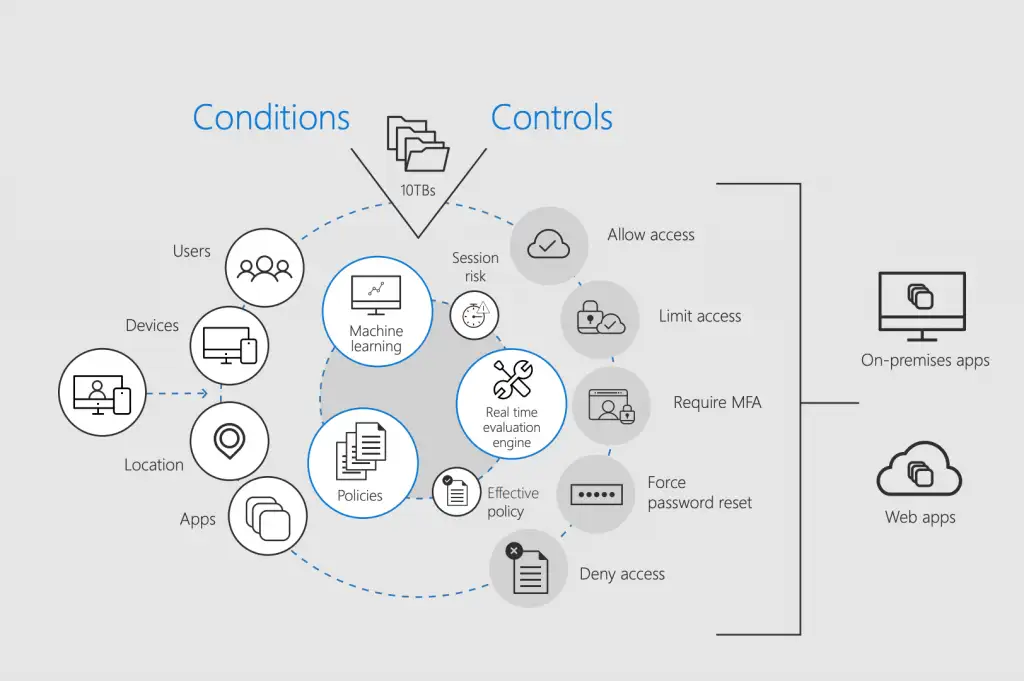 (Microsoft Corporation. 2018)
(Microsoft Corporation. 2018)
Services like Onelogin, Azure Active Directory and Practise Protect allow for a Secure Single Sign-On (Secure SSO) and remove the need to manage multiple MFA types and passwords between third party systems. When pre-existing integrations don’t already exist we can create new ones.
These services can allow us to do the following;
- Choose when MFA is applied by time, location and or type of information being accessed
- Allow access from BYOD devices while still allowing for secure content control
- Integrate multiple vendors into one platform
- Secure access to company social media and third party platforms using company credentials so employees never know the passwords
- Not use a password at all
These are all problems that can be overcome once we know how to. As a former manager of mine instilled in me Single Sign On or else. Why does it have to be any different these days with MFA? It has now evolved into Secure Single Sign-On.
References:
Microsoft Corporation. (2018). Microsoft 365 + the NIST cybersecurity framework. Retrieved from: https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2x3jO
Margosis, A. (2019, April 24). Security baseline (DRAFT) for Windows 10 v1903 and Windows Server v1903. Microsoft Tech Net. Retrieved from: https://blogs.technet.microsoft.com/secguide/2019/04/24/security-baseline-draft-for-windows-10-v1903-and-windows-server-v1903/
